How hackers are really getting your data, and what you can do to keep it safe
Follow these steps to keep your digital life secure

Another day, another hack. At least, that's how it's starting to feel.
People are getting hacked or becoming otherwise compromised in their digital lives at an alarming rate, and it seems as though that's not going to slow down any time soon.
Just earlier this month, it was revealed that hackers had gained access to millions of Twitter accounts, and not by hacking into Twitter itself. No, instead they simply gathered passwords from previous hacks and matched them with usernames.
With hackers on the rampage, there are plenty of things to keep in mind - things that will help you protect yourself and your online data, and ensure that you retain full control over your personal information.
How hackers are getting your information
Often when we think of the word "hacking", we imagine pages and pages of code, hours spent cracking away on a computer, and finding a way to get around having to use passwords. In reality, however, hackers can simply write a program that will look through information to find what they need to log in to a user's account. That's without having to spend hours at the computer combing through code.
"Hackers will most often parse existing breach data for emails, usernames, and passwords, and then attempt to reuse those credentials on popular websites," Alexander Heid, Chief Risk Officer at SecurityScorecard, a security monitoring service, tells TechRadar. "To achieve this, hackers will make use of 'checker' scripts. These are scripts which are designed to test batches of username:password combinations on specific websites to identify valid accounts. These scripts exist for every imaginable service, and are constantly updated and circulate within the hacker underground."
So, what does that mean? When you create a new account somewhere, you likely reuse at least some information for its creation. Even if you're not using the same username or password, information like answers to security questions or other details can all help hackers gain access to your account.
Get the best Black Friday deals direct to your inbox, plus news, reviews, and more.
Sign up to be the first to know about unmissable Black Friday deals on top tech, plus get all your favorite TechRadar content.

Of course, some hackers are a little more hands on. That's where malware comes in. Malware is basically a type of software designed specifically to infect your computer, often in an attempt to steal your personal information.
A prominent form of malware is a keylogger, which basically tracks everything you type and then sends that information back to the hacker who wrote the malware code. That makes it way too easy for hackers to gain access to your accounts; all they have to do is wait until you log on to something and they'll be able to do the same.
There's one more method that hackers often use to get username and password information - phishing emails. These are essentially emails designed to look like they're from a company like Apple or Amazon, and trick you into willingly giving over your information.
These scripts exist for every imaginable service, and are constantly updated and circulate within the hacker underground - Alexander Heid, Chief Risk Officer at SecurityScorecard
Often times, there's a link in these emails that will take you to an official-looking website where you're supposed to log in to an account. Only, the website isn't official, it just looks like it is. Log in, and you're basically handing your information over to whoever sent the email.
How can you stay safe?
Now that you know how hackers are acquiring personal information, it's sure to be a little easier to protect yourself. The first thing to talk about is passwords.
Make passwords a priority
As mentioned, hackers are often able to use previous data breaches to find passwords, then find accounts on other sites and use the same username:password combination to get in. That should be far too easy for hackers to get into an account, but, in reality, people continue to use the same password, or the same few passwords, for their entire digital lives.
The solution? Come up with a new password for every account you have. Yes, it's a pain, but the fact is that creating unique and secure passwords for each of your accounts is an important step in remaining secure online. Not only that, but it could help save you time in the long run; if one of your accounts is hacked, having unique passwords prevents you from having to change the password for all of your accounts.

"As witnessed with Mark Zuckerberg's [early June] hacking, using the same password across multiple sites can be convenient, but it broadens your exposure," says Bill Ho, CEO of Biscom, a secure file transfer company. "While we all have a growing number of accounts and credentials to remember, there are several good password management applications that can help."
Of course, keeping track of different passwords for everything doesn't have to be overly difficult. There are plenty of password management services out there, such as LastPass, which is perhaps the best known service. These store all of your passwords, and automatically log you in to your accounts through a browser extension.
Use antivirus software
Passwords aren't the only thing to keep an eye on - sometimes you'll unfortunately find yourself with a virus on your computer. It just happens. So, how can you protect yourself against them?

There are a few ways. I could do an entire article on how to deal with viruses, but the rundown is this: don't download files from unknown sources, don't visit suspicious websites, and use antivirus software. I personally use AVG, but there are plenty of great antivirus programs out there that scan your computer and offer real time protection. Many of them are free, too.
Be on guard against phishing scams
Phishing scams are a pretty popular way for hackers to try and get your personal information, and, if successful, the hacker doesn't have to do anything to get into your account other than send you an email.
How can you ensure that you don't fall victim to a phishing scam? There are a number of telltale signs that an email is illegitimate.
Start out by looking at the sender address. Often times the email will appear to be sent from an official source, but there will be something slightly off about it. An email from [email protected] is likely legit. An email from [email protected] is not.
When you get an email, be extremely cautious of links in that email. Often these links look like they'll take you to a legitimate website, but they'll end up taking you to a website that isn't owned by the company the hacker is trying to imitate. To check a link's actual address, hover your mouse over it and the link address should show up.
If you do decide to click on a link, there are still ways to make sure the website you're taken to is legit. Most web browsers show the website in question in green if it has a Extended Validation certificate, which basically identifies it as a legitimate business. You can see what that looks like on Chrome below.
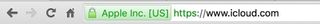
A few other things that can tip of a phishing scam is to note the greeting in the email (if it says "dear valued customer" instead of using your name, it's more likely to be a scam), checking that the email was sent to the same address that you gave the company (if Apple has your Gmail but you got the email on an Outlook email address, it's a scam), and being extremely cautious of any attachments.
Preparation is key
Keeping a realistic mindset is an important part of ensuring you don't get hacked. The safest thing to do is to assume that you will be hacked, because chances are, you will. When that does happen, it pays to be prepared and not have to change all your passwords because you used the same one for every service.
It's also important to note that following the above steps won't make you invincible - even the most security-aware can fall victim to a hacker. If, however, that does happen, following the steps above will help you take control of the situation as quickly as possible, ensuring that you don't lose more personal information than you have to, or worse.
Christian is a writer who's covered technology for many years, for sites including Tom's Guide, Android Central, iMore, CNN, Business Insider and BGR, as well as TechRadar.
